1、环境准备(k8s集群) 1 2 3 4 5 6 [root@master1 ~]
Sonarqube部署机器ip:192.168.101.12
nexus部署机器ip:192.168.101.12
gitlab部署机器ip:192.168.101.12
harbor部署机器ip:35.220.201.102
2、Jenkins安装 Jenkins安装的是2.379版本;
Kubernetes集群版本是1.25.0
2.1 配置nfs服务(node1上) 1 2 3 4 5 6 [root@node1 ~]
2.2 制作Jenkins 2.379镜像 1 2 3 4 5 6 7 8 9 10 11 12 [root@node1 dockerfile]"jenkins/jenkins:2.379" .
由于1.25.0采用的是containerd来管理的容器,制作好的镜像要在docker中导出保存,然后导入containerd中
1 2 3 4 5 6 7 8 9 10 11 [root@node1 ~]
2.3 创建挂载卷(pv与pvc) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 [root@master1 jenkins_gitlab_springcloud_harbor_nexus_k8s_Devops]
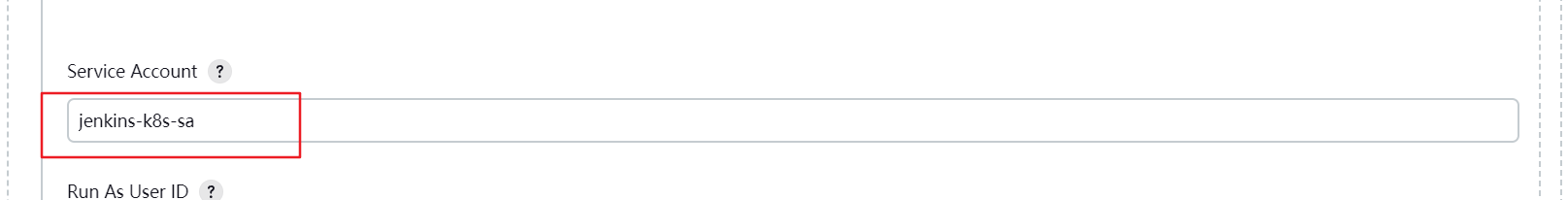
2.4 创建sa账号并作授权(master节点) 1 2 3 kubectl create ns jenkins-k8s
3.5 部署Jenkins 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 [root@master1 jenkins_gitlab_springcloud_harbor_nexus_k8s_Devops]
3.6 解决出现的报错(node1上) 1 chown -R 1000.1000 /nfs-data/v2
3.7 配置svc四层代理 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 [root@master1 jenkins_gitlab_springcloud_harbor_nexus_k8s_Devops]type : NodePort
1 2 3 4 5 6 7 8 [root@master1 ~]
3、Jenkins的配置 3.1 安装插件 kubernetes插件
blueocean插件
注意 :安装完插件需要重启才能生效
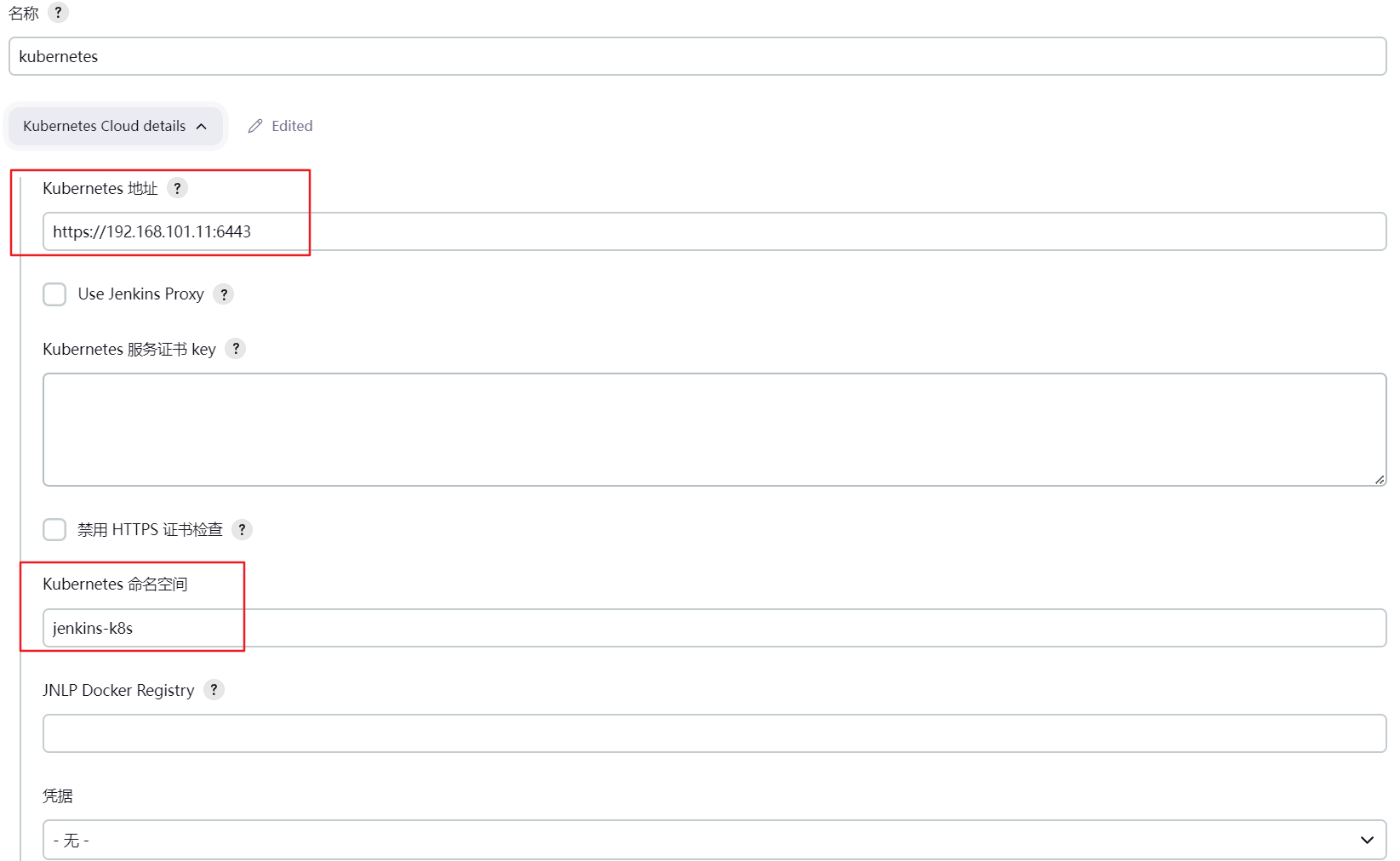
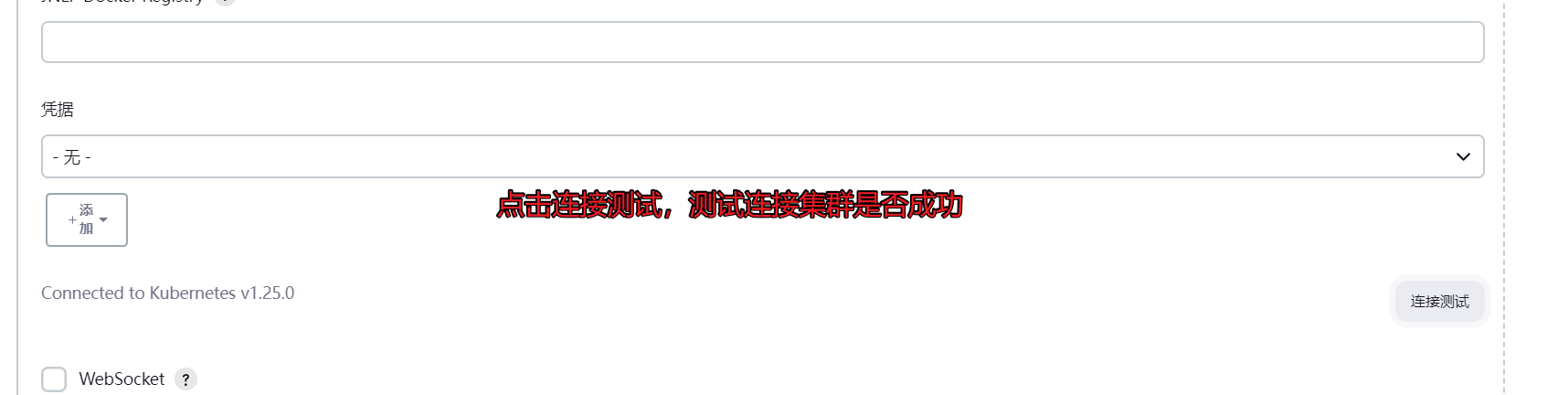
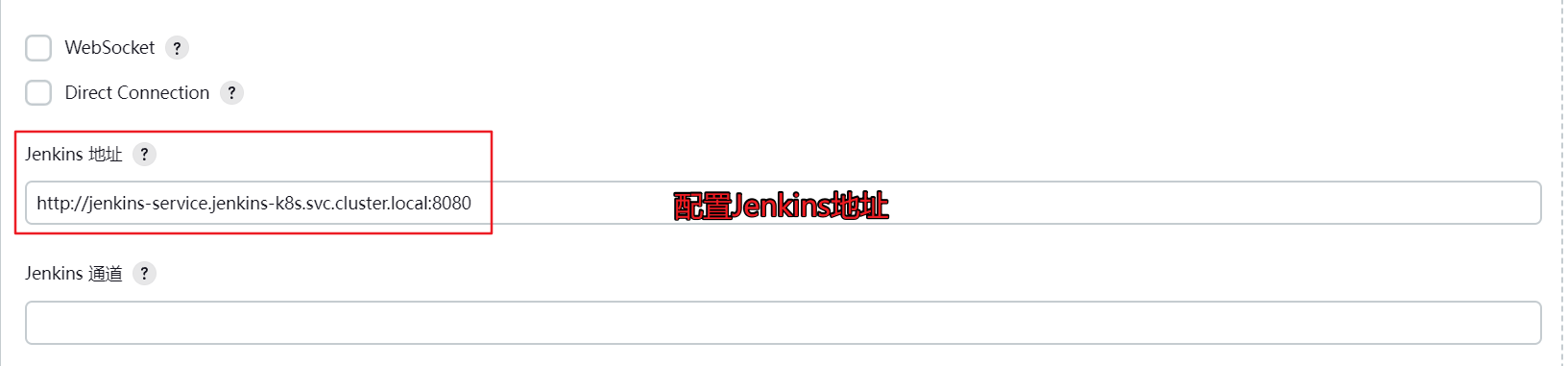
3.2 配置连接kebernetes集群 访问http://192.168.101.11:30002/configureClouds/
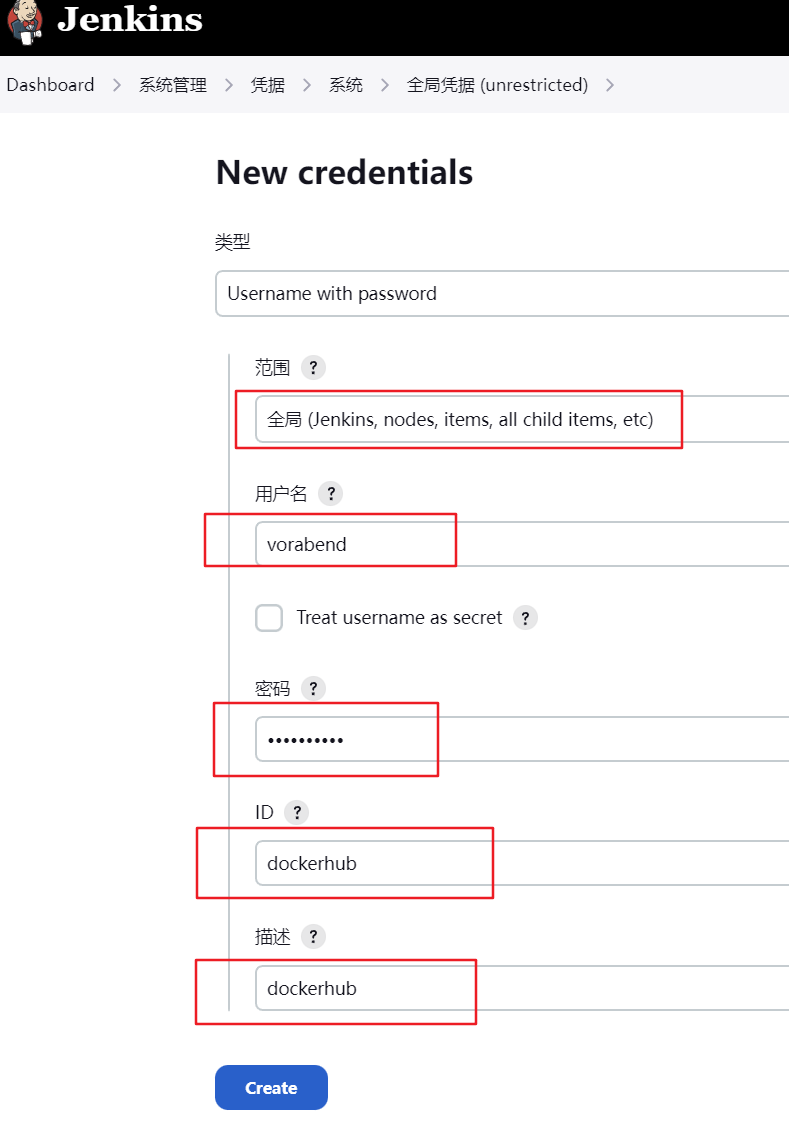
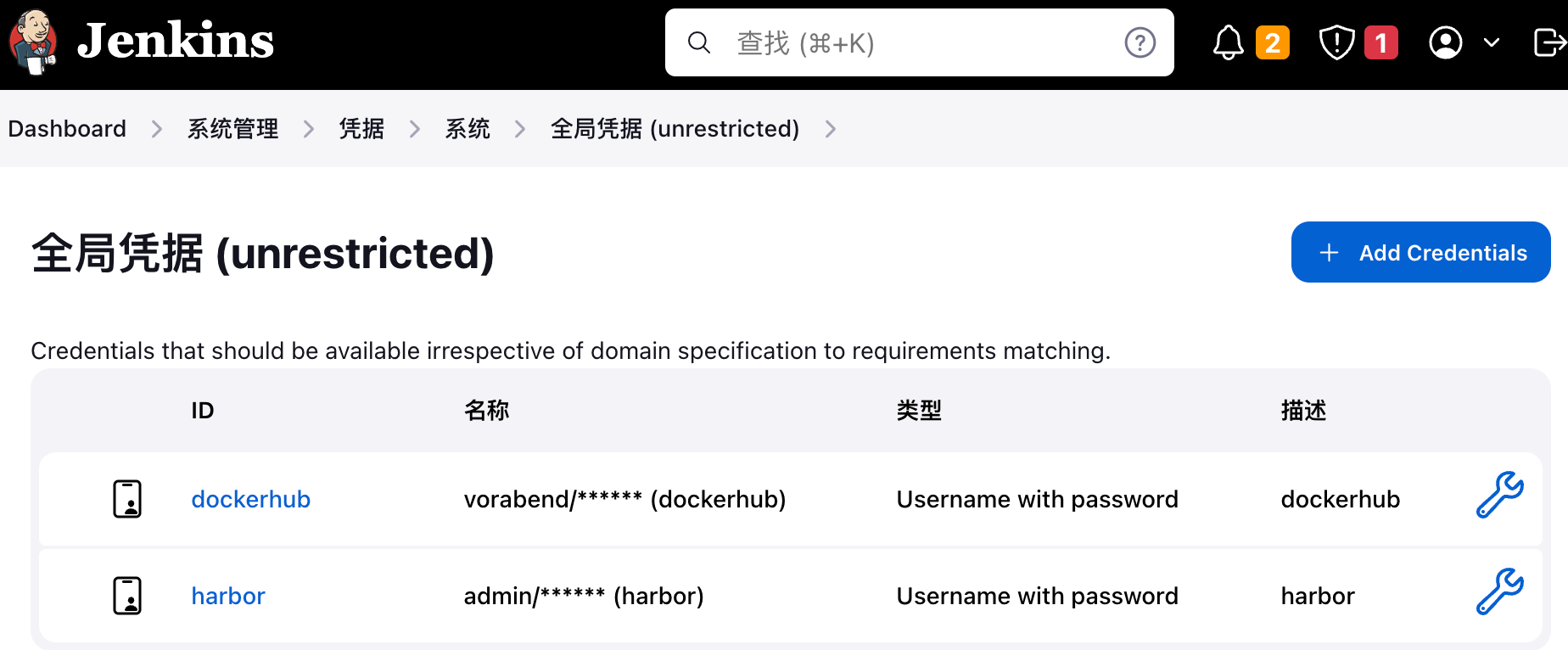
3.3 添加dockerhub凭据
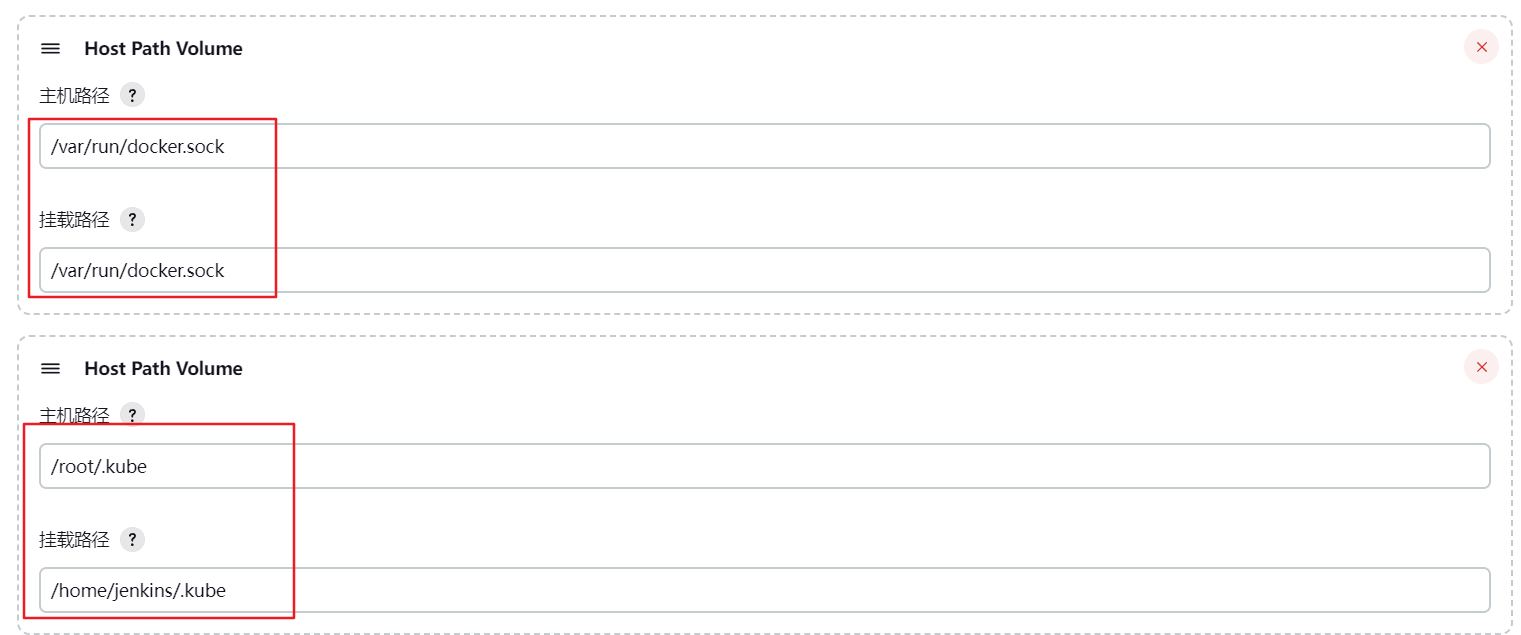
3.4 拷贝.kube文件到node节点上 1 2 [root@master1 ~]
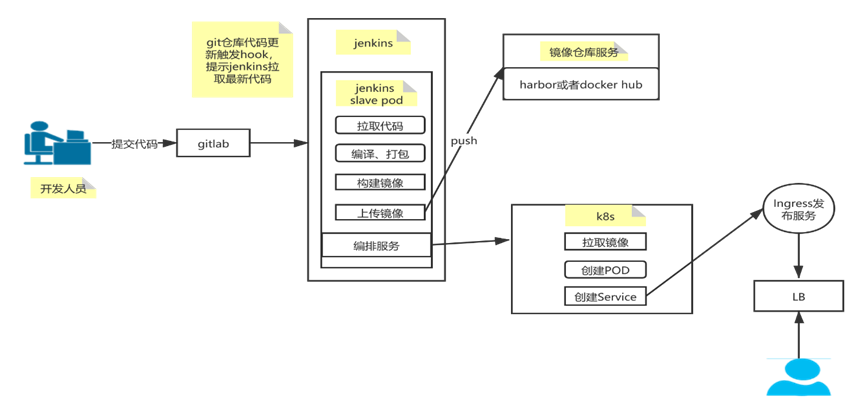
4、测试通过Jenkins部署应用发布到k8s开发、生产、测试环境 开发提交代码到代码仓库gitlab—->jenkins检测到代码更新—–>调用k8s api在k8s中创建jenkins slave pod:
Jenkins slave pod拉取代码—–>通过maven把拉取的代码进行构建成war包或者jar包—>上传代码到Sonarqube,进行静态代码扫描- –>基于war包构建docker image–>把镜像上传到harbor镜像仓库–>基于镜像部署应用到开发环境–>部署应用到测试环境—>部署应用到生产环境。
4.1 创建所需名称空间 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 [root@master1 ~]
4.2 制作Jenkins-agent镜像 注意: 要在能科学上网的节点上进行操作
由于从官方下载的Jenkins-agent中无docker、kubectl命令,且其中的/var/run/docker.sock
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 [root@harbor dockerfile]"deb [arch=amd64] https://download.docker.com/linux/$(. /etc/os-release; echo "$ID " ) $(lsb_release -cs) stable" && \"https://github.com/docker/compose/releases/download/1.26.2/docker-compose-$(uname -s) -$(uname -m) " -o /usr/local /bin/docker-compose \local /bin/docker-compose \local /bin/docker-compose /usr/bin/docker-compose \echo "deb https://apt.kubernetes.io/ kubernetes-xenial main" | tee /etc/apt/sources.list.d/kubernetes.list \$HOST_GID dockerfor docker.io/jenkins/inbound-agent:latest 0.0s"https://github.com/docker/compose/releases/download/1.26.2/docker-compose-$(una 0.0s => [4/6] RUN echo "deb https://apt.kubernetes.io/ kubernetes-xenial main" | tee /etc/apt/sources.list.d/kube 6.0s => [5/6] RUN groupmod -g 991 docker 0.7s => [6/6] RUN usermod -aG docker jenkins 0.5s => exporting to image 8.1s => => exporting layers 8.1s => => writing image sha256:81bfceafc0e69eaa425523f4b8749a8b31eb0041afd14991efe38935f5182f20 0.0s => => naming to docker.io/jenkins/jnlp:v1 0.0s #将镜像导入node节点中 [root@node1 ~]# ctr -n k8s.io image import jenkins-jnlp-v1.tar unpacking docker.io/jenkins/jnlp:v1 (sha256:659a7d21499b44da44f6fc72bd40bbed36a527b19d37cff75c51037632434fcb) ...done
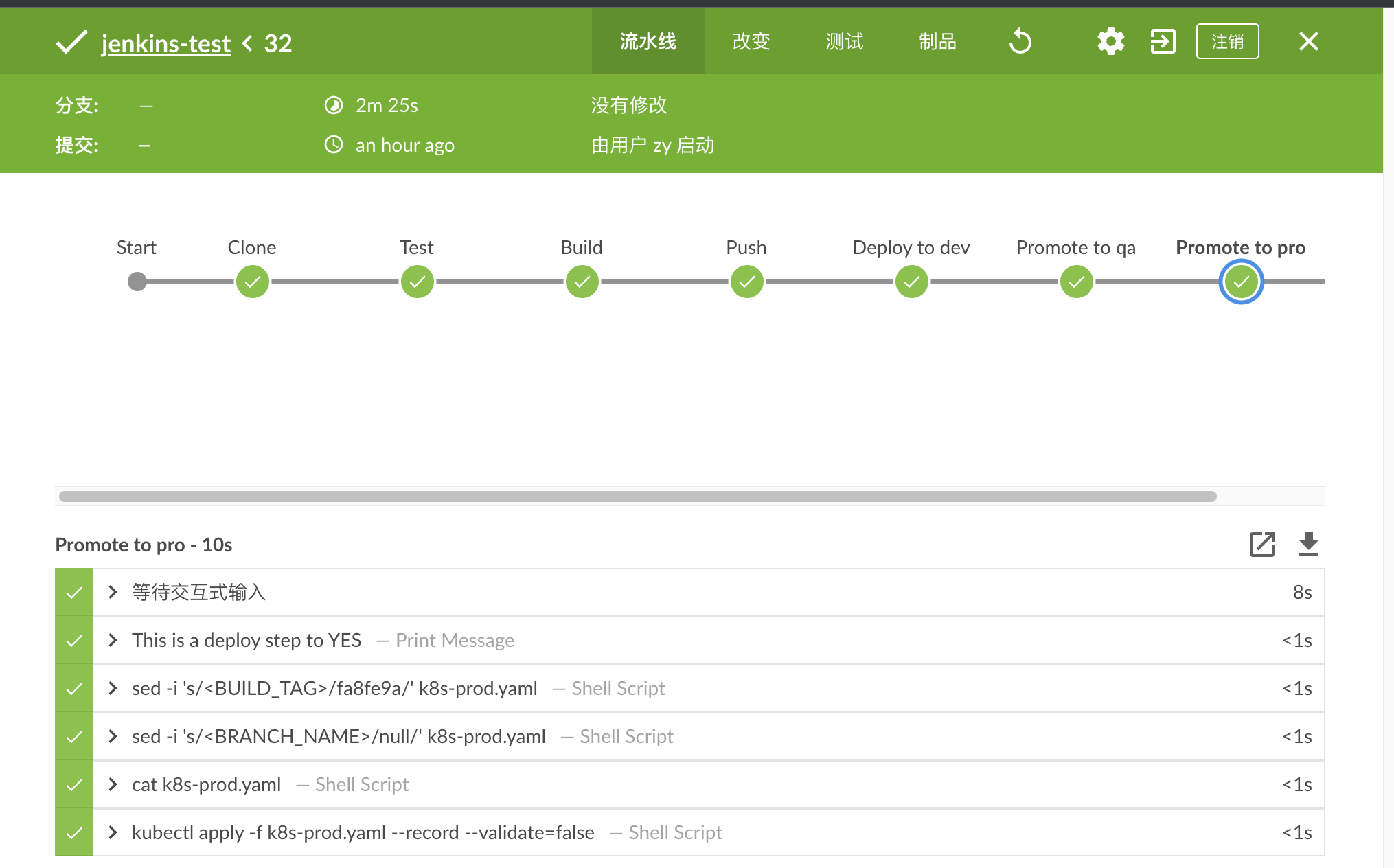
4.3 新建pipeline脚本 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 node('test' ) {'Clone' ) {echo "1.Clone Stage" "https://kgithub.com/vorabend/jenkins-sample.git" true , script: 'git rev-parse --short HEAD' ).trim()'Test' ) {echo "2.Test Stage" 'Build' ) {echo "3.Build Docker Image Stage" "docker build -t vorabend/jenkins-demo:${build_tag} ." 'Push' ) {echo "4.Push Docker Image Stage" 'dockerhub' , passwordVariable: 'dockerHubPassword' , usernameVariable: 'dockerHubUser' )]) {"docker login -u ${dockerHubUser} -p ${dockerHubPassword} " "docker push vorabend/jenkins-demo:${build_tag} " 'Deploy to dev' ) {echo "5. Deploy DEV" "sed -i 's/<BUILD_TAG>/${build_tag} /' k8s-dev.yaml" "sed -i 's/<BRANCH_NAME>/${env.BRANCH_NAME} /' k8s-dev.yaml" "bash running-devlopment.sh" "kubectl apply -f k8s-dev.yaml --validate=false" 'Promote to qa' ) { 'userInput' ,'Promote to qa?' ,$class : 'ChoiceParameterDefinition' ,"YES\nNO" ,'Env' echo "This is a deploy step to ${userInput} " if (userInput == "YES" ) {"sed -i 's/<BUILD_TAG>/${build_tag} /' k8s-qa.yaml" "sed -i 's/<BRANCH_NAME>/${env.BRANCH_NAME} /' k8s-qa.yaml" "bash running-qa.sh" "kubectl apply -f k8s-qa.yaml --validate=false" "sleep 6" "kubectl get pods -n qatest" else {exit 'Promote to pro' ) { 'userInput' ,'Promote to pro?' ,$class : 'ChoiceParameterDefinition' ,"YES\nNO" ,'Env' echo "This is a deploy step to ${userInput} " if (userInput == "YES" ) {"sed -i 's/<BUILD_TAG>/${build_tag} /' k8s-prod.yaml" "sed -i 's/<BRANCH_NAME>/${env.BRANCH_NAME} /' k8s-prod.yaml" "bash running-production.sh" "cat k8s-prod.yaml" "kubectl apply -f k8s-prod.yaml --record --validate=false"
4.4 运行pipeline脚本 全部运行成功
通过上面Jenkins对接K8S,就可以把应用发送到K8S集群的开发、测试、生产环境中去了
1 2 3 4 5 6 [root@master1 ~]
5、配置拉取harbor镜像仓库 由于采用的k8s版本是1.25.0,此版本k8s已经不使用docker作为容器运行时,而是采用containerd作为容器运行时,但是一般情况下我们docker也需要安装,因为需要制作镜像。
5.1 修改配置文件(config.toml与hosts) master和node所有节点上修改/etc/containerd文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 cd /etc/containerd"io.containerd.grpc.v1.cri" .registry]"" "io.containerd.grpc.v1.cri" .registry.mirrors]"io.containerd.grpc.v1.cri" .registry.mirrors."docker.io" ]"https://registry.cn-hangzhou.aliyuncs.com" ]"io.containerd.grpc.v1.cri" .registry.mirrors."35.220.201.102" ]"http://35.220.201.102" ]"io.containerd.grpc.v1.cri" .registry.configs]"io.containerd.grpc.v1.cri" .registry.configs."35.220.201.102" .tls]true "io.containerd.grpc.v1.cri" .registry.configs."35.220.201.102" .auth]"admin" "harbor的密码"
5.2 测试拉取镜像是否成功 1 2 [root@master1 ~]for sha256:65d9615ad919f1704881006d8de94f67e23e93173ef0edb97bad0953d72ef49b
6、安装sonarqube SonarQube 是一个开源的代码分析平台, 用来持续分析和评测项目源代码的质量。 通过SonarQube我们可以检测出项目中重复代码, 潜在bug, 代码规范,安全性漏洞等问题, 并通过SonarQube web UI展示出来。
6.1 调整vm.max_map_count参数的大小 max_map_count文件包含限制一个进程可以拥有的VMA(虚拟内存区域)的数量
1 2 3 4 5 6 7 8 9 10 [root@master2 ~]
6.2 上传与解压postgres.tar.gz sonarqube.tar.gz镜像文件 1 2 3 4 5 [eve-ng 课程资料] $ scp postgres.tar.gz sonarqube.tar.gz 192.168.101.12:~
6.3 运行容器 1 2 3 4 5 [root@master2 ~]
6.4 浏览器访问sonarqube 默认的账号密码都是admin
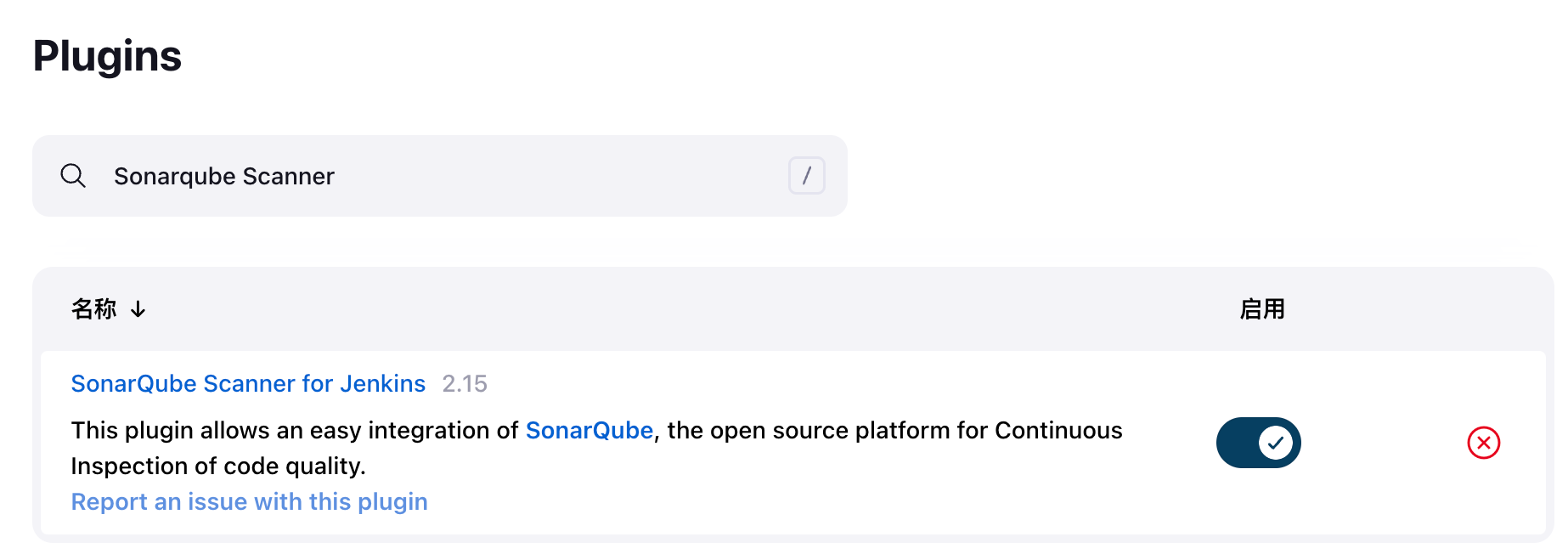
6.5 在jenkins中安装sonarqube插件 在jenkins中安装sonarqube插件:
系统管理->插件管理->可选插件:搜索sonar,找到Sonarqube Scanner->选择Sonarqube Scanner直接安装,安装之后重启jenkins即可:
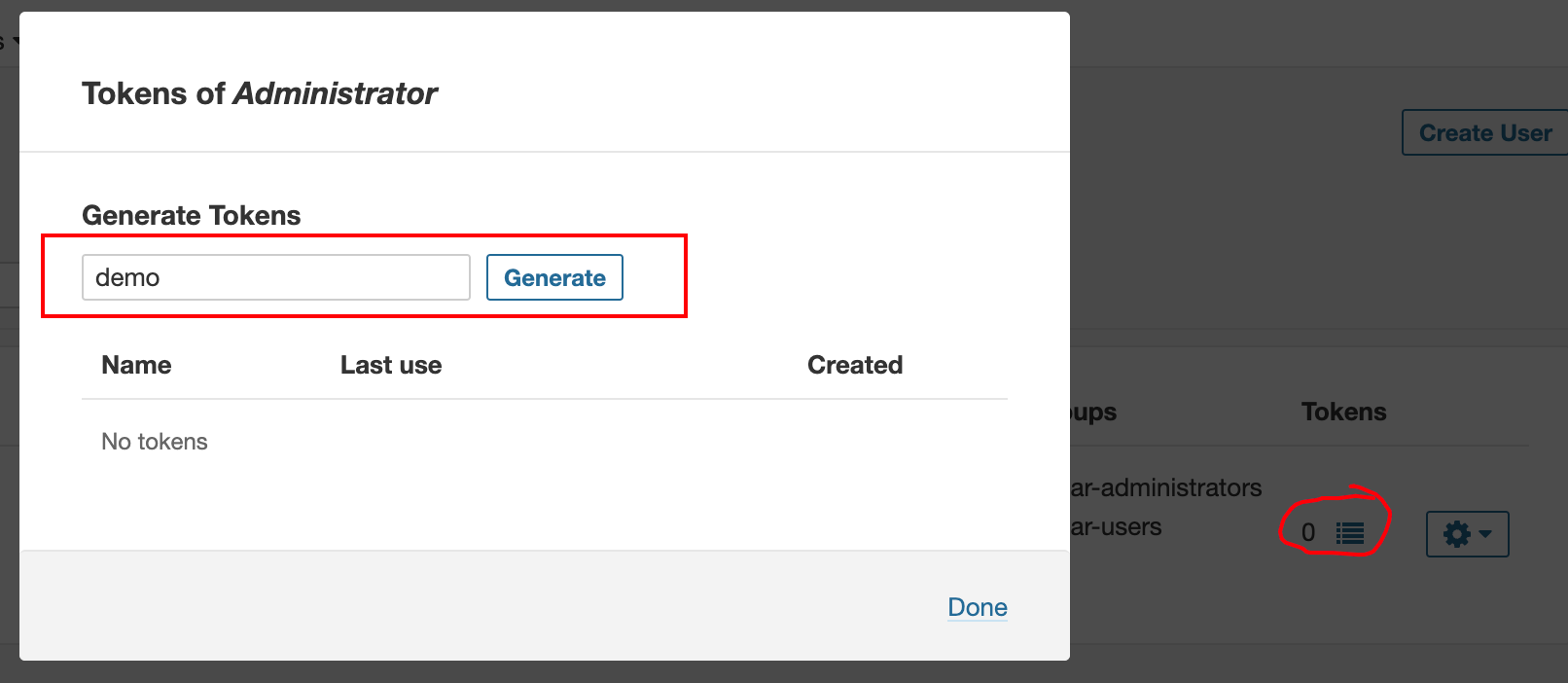
6.6 在sonarqube的web界面上创建一个token
1 2
6.5 将源码包上传到控制节点编译打包 1 2 3 4 5 [root@master1 jenkins_gitlab_springcloud_harbor_nexus_k8s_Devops]
7、Jenkins界面添加harbor凭据
8、安装nexus 概念:
Nexus服务器是一个代码包管理的服务器,可以理解 Nexus 服务器是一个巨大的 Library 仓库。Nexus 可以支持管理的工具包括 Maven , npm 等,对于 JAVA 开发来说,只要用到 Maven 管理就可以了。
Nexus服务器作用:因为传统的中央仓库在国外,其地理位置比较远,下载速度比较缓慢。因此,当公司开发人员数量越来越多时,如果不架设一台自己的Nexus服务器,会产生大量的流量阻塞带宽,并且在出现一些不可抗原因(光缆被挖断)导致无法连接到中央仓库时,开发就会因为无法下载相关依赖包而进度停滞。因此在本地环境部署一台私有的Nexus服务器来缓存所有依赖包,并且将公司内部开发的私有包也部署上去,方便其他开发人员下载,是非常有必要的。因为 Nexus 有权限控制,因此外部人员是无法得到公司内部开发的项目包的。
8.1 解压镜像启动容器 1 2 3 4 5 6 7 8 9 [root@master2 ~]
8.2 使用nexus 第一步:
1、在 pom.xml 文件中声明发布的宿主仓库和 release 版本发布的仓库。
1 2 3 4 5 6 7 8 9 10 11 12 13 <!-- 发布构件到Nexus -->
第二步:在 settings.xml 文件中配置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <servers>
注意: settings.xml 中 server 元素下 id 的值必须与 POM 中 repository 或 snapshotRepository 下 id 的值完全一致 。
9、安装gitlab 9.1 导入镜像启动容器 1 2 3 4 5 6 [root@master2 ~]
9.2 修改gitlab的配置文件重启docker 1 2 3 4 5 6 7 [root@master2 config]'http://192.168.101.12' 'gitlab_ssh_host' ] = '192.168.101.12' 'gitlab_shell_ssh_port' ] = 222
9.3 进入gitlab容器中修改账号密码 登录账号:root
登陆密码:12345678
确保Jenkins中安装了Gitlab插件
1 2 3 4 5 6 [root@master2 ~]'12345678' '12345678'
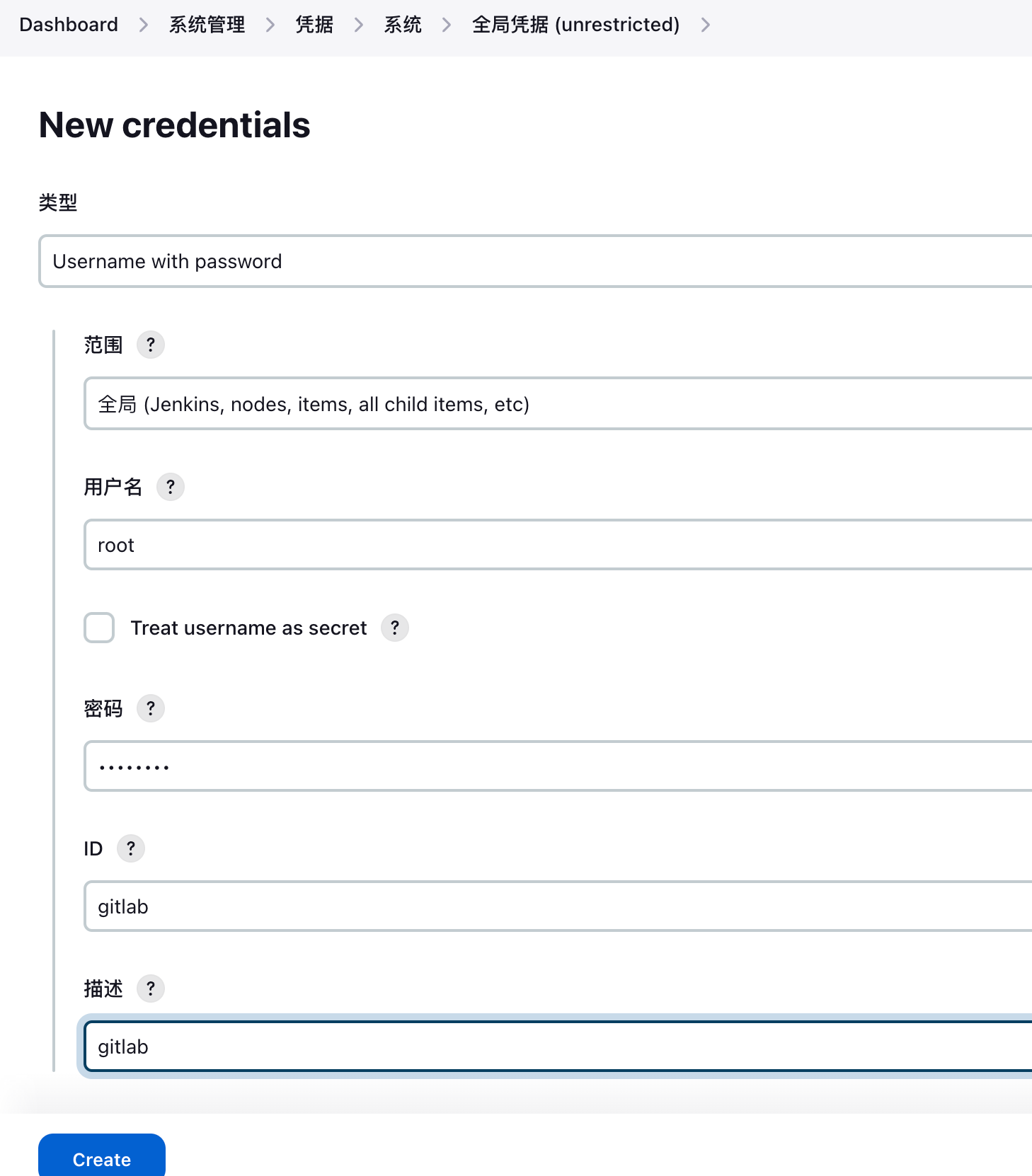
9.4 Jenkins界面添加gitlab凭据
9.5 登录gitlab新建项目上传代码
1 2 3 4 5 6 7 8 git config --global user.email "792548841@qq.com" "ZhangYu" for 'http://192.168.101.12' : rootfor 'http://root@192.168.101.12' : 'master' set up to track 'origin/master' .
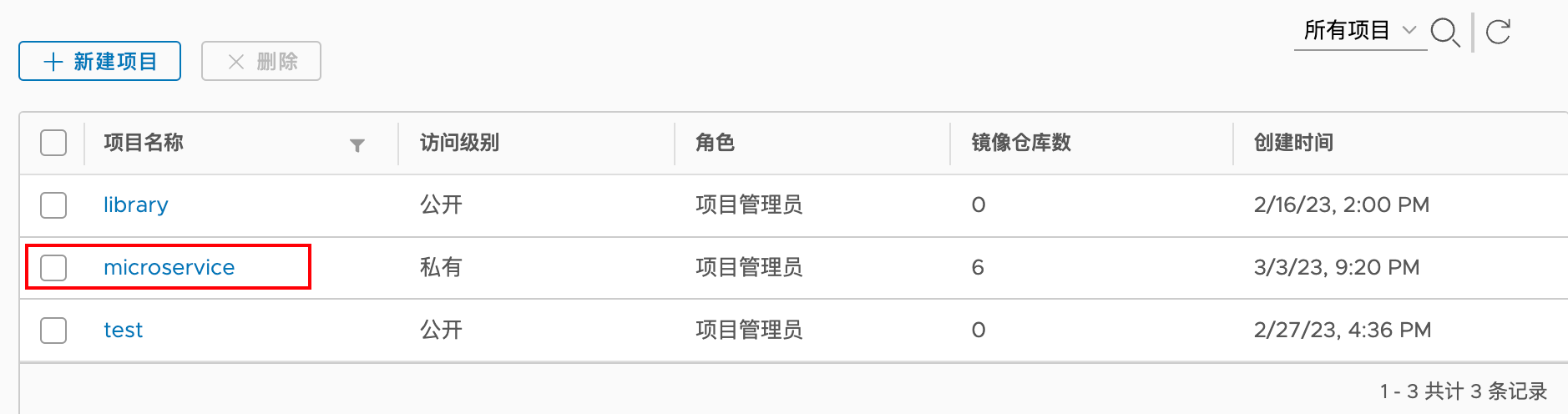
10、构建Devops 10.1 在harbor仓库上创建一个项目(microservice )
10.2 创建拉取harbor私有仓库镜像的secert 10.3 导入docker.io/jenkins/jnlp:v2镜像(node节点) 通过dockerfile构建镜像,里面封装了docker、kubectl、maven.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 [root@harbor dockerfile]"deb [arch=amd64] https://download.docker.com/linux/$(. /etc/os-release; echo "$ID " ) $(lsb_release -cs) stable" && \"https://github.com/docker/compose/releases/download/1.26.2/docker-compose-$(uname -s) -$(uname -m) " -o /usr/local /bin/docker-compose \local /bin/docker-compose \local /bin/docker-compose /usr/bin/docker-compose \echo "deb https://apt.kubernetes.io/ kubernetes-xenial main" | tee /etc/apt/sources.list.d/kubernetes.list \$HOST_GID docker
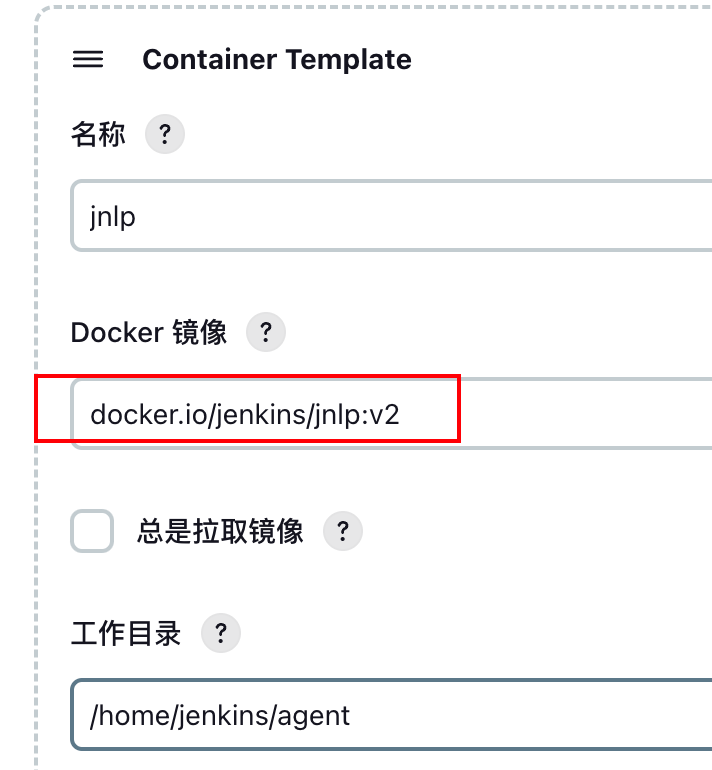
10.4 更改jenkins模版的镜像为docker.io/jenkins/jnlp:v2
10.5 修改gitlab上的portal.yaml 把image镜像变成:35.220.201.102/microservice/jenkins-demo:v1
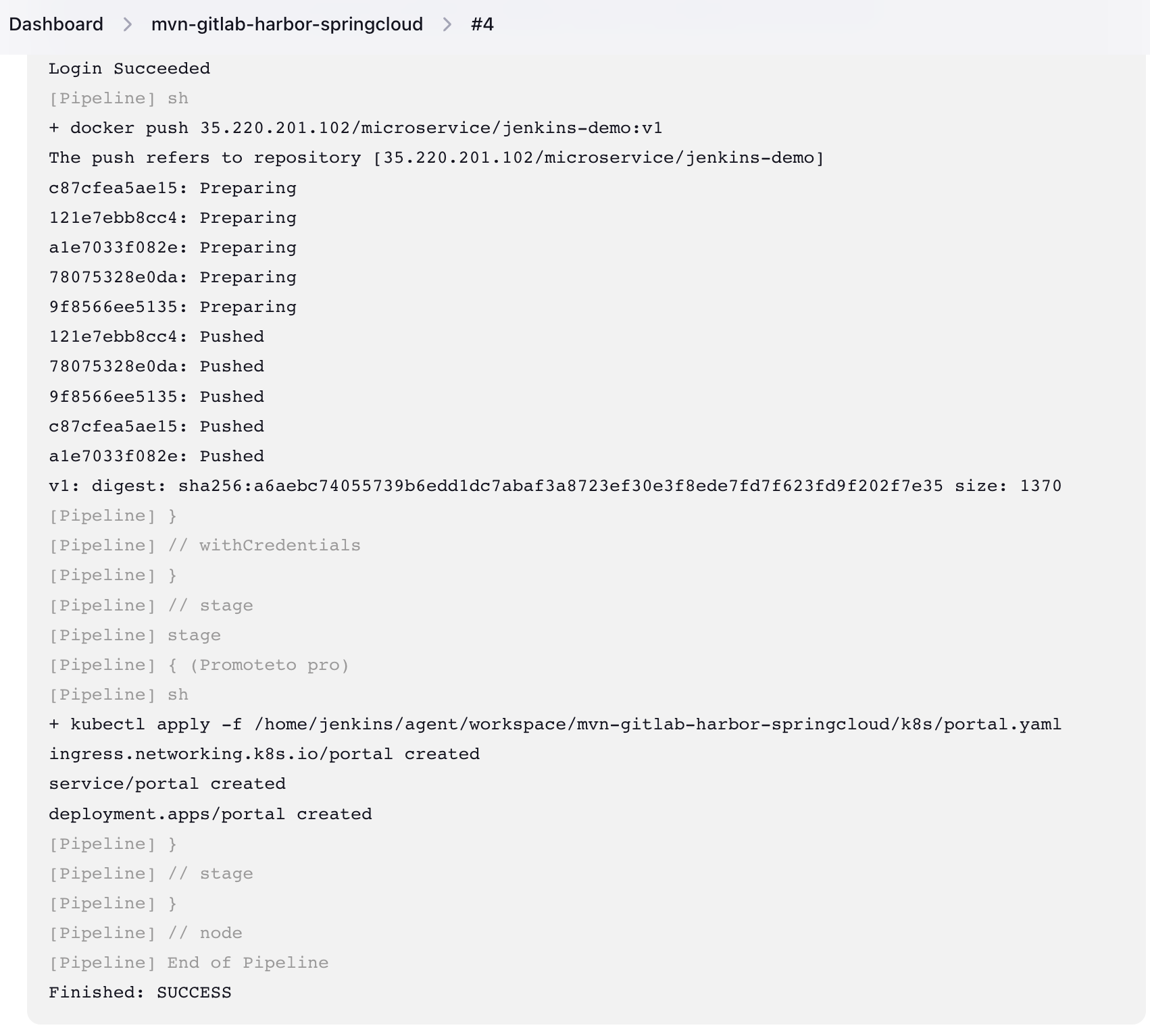
10.6 编写pipeline脚本 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 node('test' ) {'Clone' ) {echo "1.Clone Stage" 'gitlab' , url: 'http://192.168.101.12/root/microservice-test.git' true , script: 'git rev-parse --shortHEAD' ).trim()'Test' ) {echo "2.Test Stage" 'mvn' ) {"mvn clean package -D maven.test.skip=true" 'Build' ) {echo "3.Build Docker Image Stage" "cd /home/jenkins/agent/workspace/mvn-gitlab-harbor-springcloud/portal-service" "docker build --tag 35.220.201.102/microservice/jenkins-demo:v1 /home/jenkins/agent/workspace/mvn-gitlab-harbor-springcloud/portal-service/" 'Push' ) {echo "4.Push Docker Image Stage" 'harbor' ,passwordVariable: 'dockerHubPassword' , usernameVariable: 'dockerHubUser' )]) {"docker login 35.220.201.102 -u ${dockerHubUser} -p ${dockerHubPassword} " "docker push 35.220.201.102/microservice/jenkins-demo:v1" 'Promoteto pro' ) { "kubectl apply -f /home/jenkins/agent/workspace/mvn-gitlab-harbor-springcloud/k8s/portal.yaml"